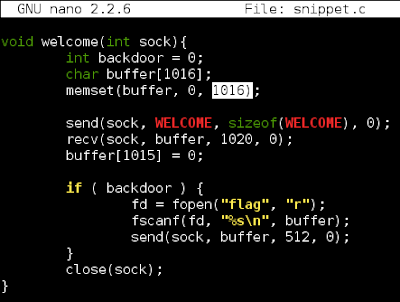
Go Hunting for Malware
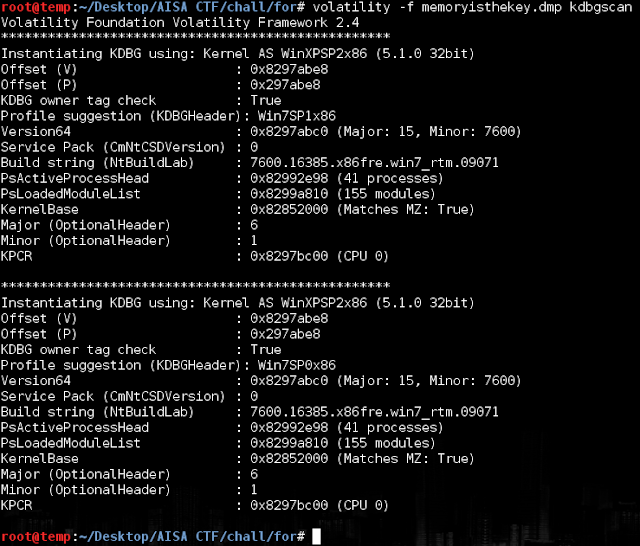
Another Interesting Challenge from AISA CTF that I would like to blog about, is the final forensic challenge to find the following information, out of a malware infected system's memory dump The Process ID of the malicious process ? The Process ID of any spawned child processes ? The date and time of when the initial Process ID was created ? The attackers IP address ? The port number the victim is connecting back to ? The URL the user visited that let to the initial infection ? And was provided with the memory dump "memoryisthekey.dmp" So the above file is a RAM dump of the system after the infection, so then volatility is the best tool in further analyzing the dump First we need to identify what profile we need to use with volatility. example: WINXP or 7, etc So then i picked "Win7SP0x86", since there was not much changes between SP1 and SP0 memory storage Lets check the process tree to identify the malicious process Now the following processes were the ones i ...