Code review and Exploit
As a part of the exploitation challenge in AISA 2015 CTF was given connection details to an server & code which the server is running. Goal is to exploit and find an 64 bit flag
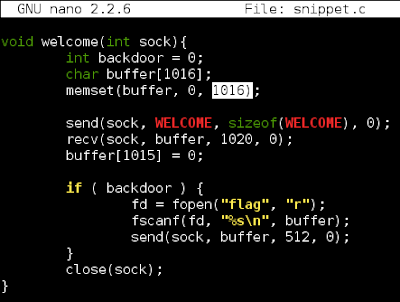
Code snippet the server running
File "my_stack", upon execution locally the following is the result
This specific code has where exactly 1016 random bytes would print us the flag as per our "if" clause in the code snippet
Now lets create an string of 1016 bytes
Time to connect to the server and exploit
We can see the 64 bit flag has been printed as per the code.
Now we can further use the memory space to host our own payload for persistance.






Comments
Post a Comment